Abstract
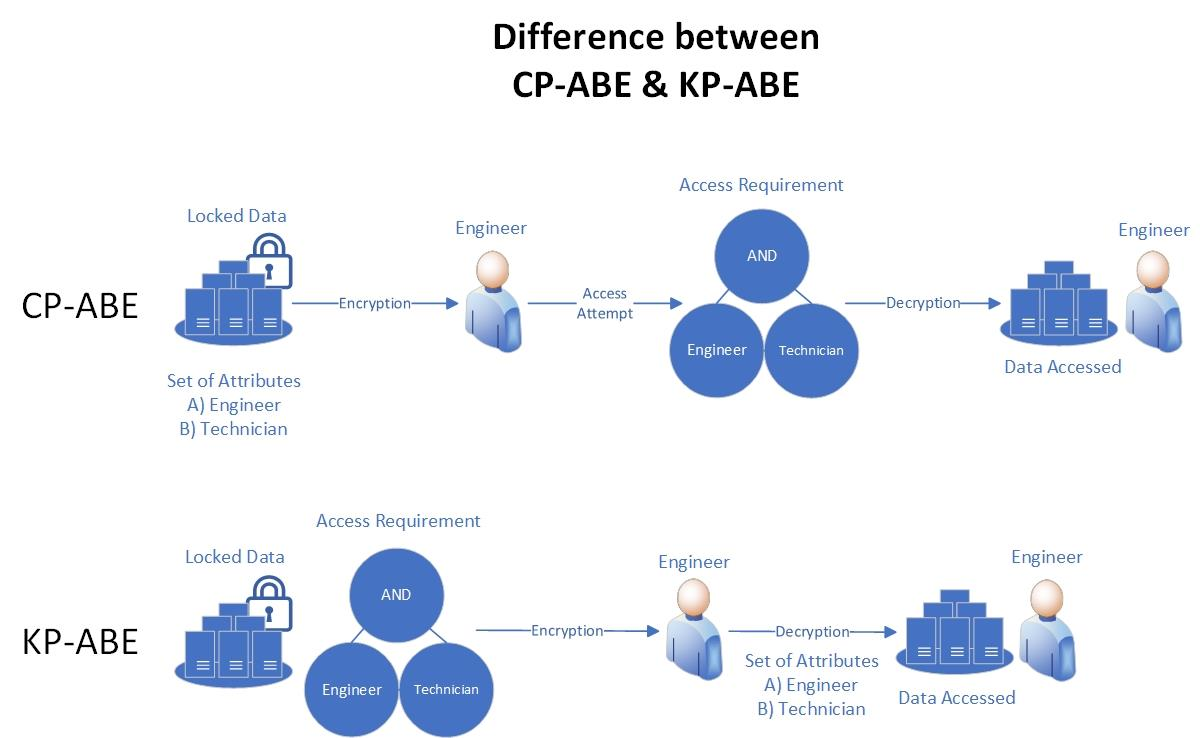
The sharing of data and private information has been greatly improved by Industry 4.0's broad usage of cloud technologies. In their quest to improve their services, many firms have made automation and effective authentication a priority. As a result, in Industry 4.0, Attribute-Based Encryption (ABE) and Attribute-Based Authentication (ABA) have established themselves as dependable models for data sharing across cloud environments. For difficult situations like fine-grained access control and secure authentication, these models offer practical answers. Organizations can utilize ABA to specifically authenticate people based on their attributes, ensuring appropriate and safe access to critical data. Despite the significance of ABE and ABA within Industry 4.0 and the wide range of applications that they have, systematic and thorough studies that include all variations of these models, as well as their historical and present condition, are lacking in the literature. This paper offers a complete and organized evaluation of works on Industry 4.0 by ABE and ABA. Our study's methodology, findings, and suggested follow-up work will advance the field of ABE and ABA research and improve the safety of data sharing in Industry 4.0. Organizations working within Industry 4.0 can improve the security of their cloud-based systems by integrating attribute-based authentication mechanisms and machine learning, making sure that only vetted individuals have access to sensitive data. ABE and ABA architectures in safe data-sharing situations within Industry 4.0, as well as the potential of ABE and ABA deployment in the context of the most recent technical breakthroughs, will also be better understood by researchers and practitioners with the aid of this study.
Funding
This work was supported without any funding.
Cite This Article
APA Style
Saleem, J., Raza, U., & Holderbaum, W. (2024). Transforming Industry 4.0 Security: Analysis of ABE and ABA Technologies. IECE Transactions on Intelligent Systematics, 1(3), 127-144. https://doi.org/10.62762/TIS.2024.993235
Publisher's Note
IECE stays neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Institute of Emerging and Computer Engineers (IECE) or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.


 Submit Manuscript
Edit a Special Issue
Submit Manuscript
Edit a Special Issue