Abstract
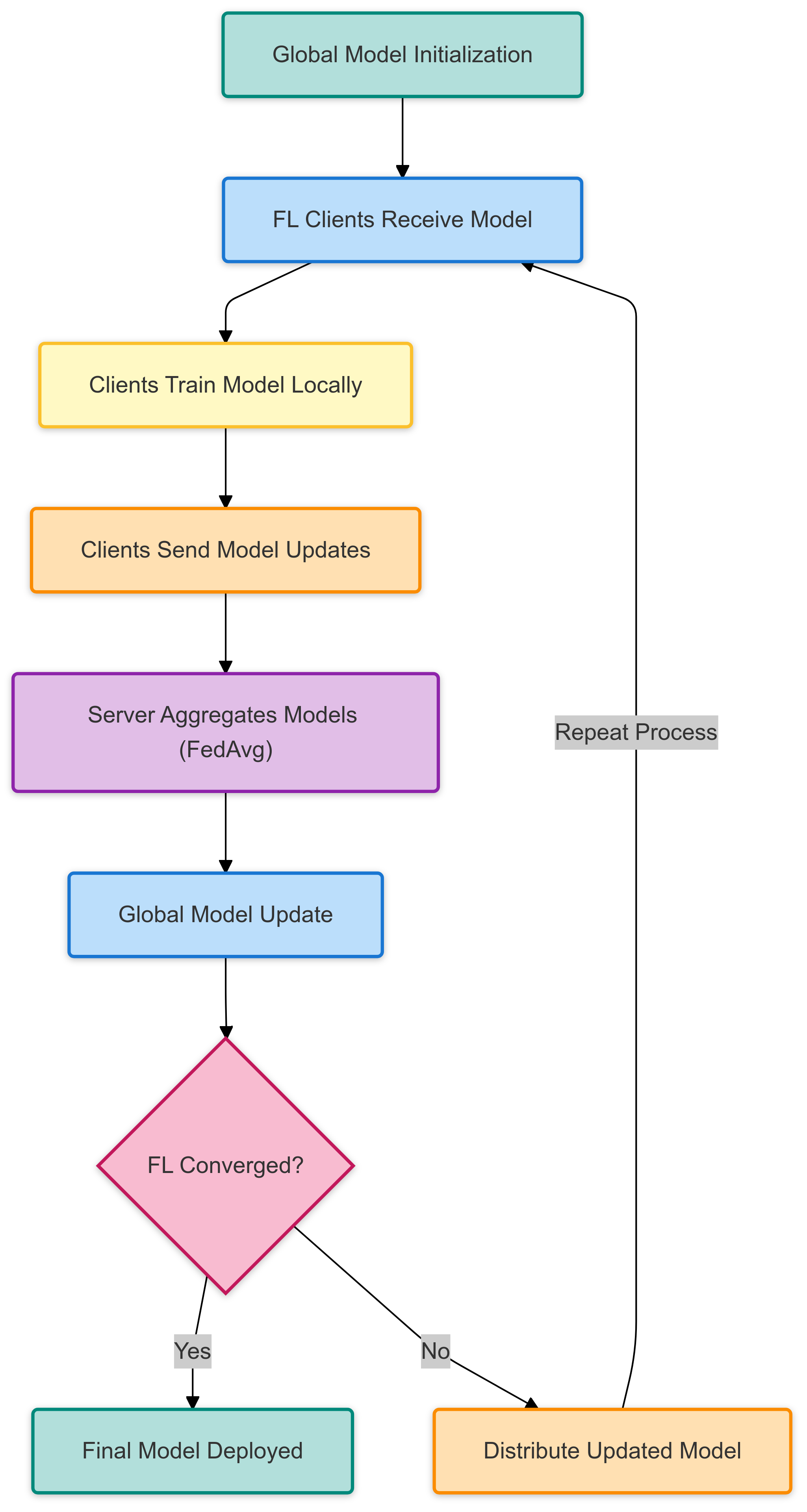
Traditional centralized machine learning approaches for IoT botnet detection pose significant privacy risks, as they require transmitting sensitive device data to a central server. This study presents a privacy-preserving Federated Learning (FL) approach that employs Federated Averaging (FedAvg) to detect prevalent botnet attacks, such as Mirai and Gafgyt, while ensuring that raw data remain on local IoT devices. Using the N-BaIoT dataset, which contains real-world benign and malicious traffic, we evaluated both the IID and non-IID data distributions to assess the effects of decentralized training. Our approach achieved 97.5% accuracy in IID and 95.2% in highly skewed non-IID scenarios, closely matching centralized learning performance while preserving privacy. Additionally, communication optimization techniques—Top-20\% gradient sparsification and 8-bit quantization—reduce communication overhead by up to 80%, significantly enhancing the efficiency. Our convergence analysis further shows that FedAvg remains effective under non-IID conditions, thereby demonstrating its robustness for real-world deployments. These results demonstrate that FL provides a scalable and privacy-preserving solution for securing IoT networks against botnet threats.
Keywords
federated learning
federated averaging (FedAvg)
privacy-preserving machine learning
IoT Security
botnet detection
edge AI
Data Availability Statement
Data will be made available on request.
Funding
This work was supported without any funding.
Conflicts of Interest
The authors declare no conflicts of interest.
Ethical Approval and Consent to Participate
Not applicable.
Cite This Article
APA Style
Myakala, P. K., Kamatala, S., & Bura, C. (2025). Privacy-Preserving Federated Learning for IoT Botnet Detection: A Federated Averaging Approach. IECE Transactions on Machine Intelligence, 1(1), 6–16. https://doi.org/10.62762/TMI.2025.796490
Publisher's Note
IECE stays neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Institute of Emerging and Computer Engineers (IECE) or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.


 Submit Manuscript
Edit a Special Issue
Submit Manuscript
Edit a Special Issue